Latest News

What is cyber security auditing?
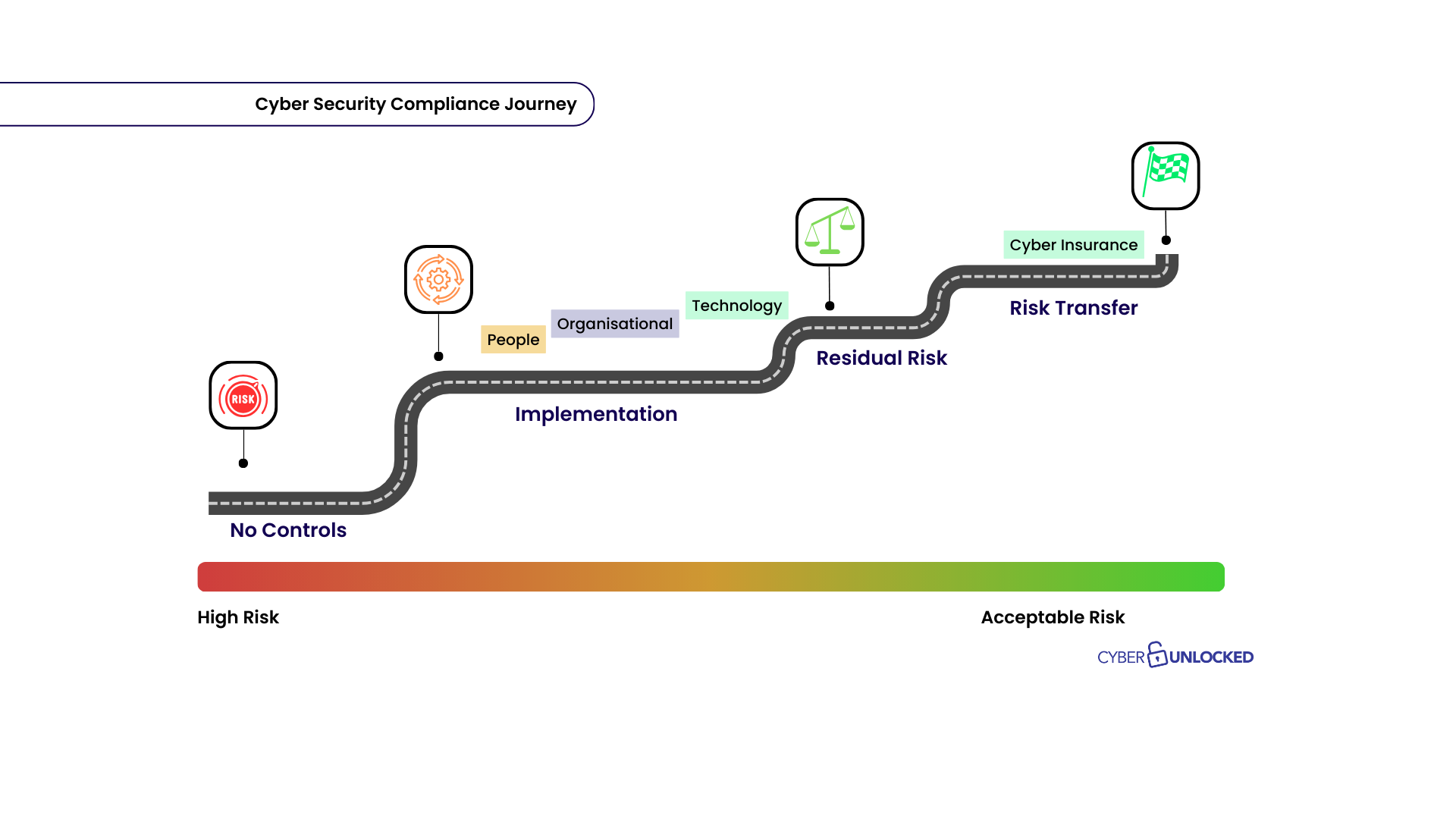
Cyber security auditing or vulnerability scanning is a foundational strategy to keep your business safe and with its help, businesses of any size can mitigate security issues and patch weaknesses. Simply, it is the process of identifying and reporting on security vulnerabilities in your business systems. Security professionals like CyberUnlocked can perform a series of tests to identify any liabilities within your systems. This can range from sensitive information being exposed to unauthorised data access that can lead to threats to your business.
How to perform a cyber security audit?
Most audits start with creating an inventory of your IT components (firewalls, servers, desktops, virtual machines, cloud workspaces) connected to your company’s network or being used by your employees. This goes beyond identifying the devices and systems, to inventorying the operating systems, the user accounts and installed software. This is usually done by an information security auditor such as CyberUnlocked who can identify known and unknown devices connected to your systems.
Once all the devices and systems have been identified, cyber security scans are run to assess and study the potential weaknesses in the IT environment and the degrees of risk that are being held by the business.
How do I know what cyber security scan to run?
Different types of cyber security scans can be conducted on your business systems. These include network scans, website scans, host scans, cloud scans, application scans, database scans, and penetration tests, to name a few. Each tackle different areas of cyber security concerns for your business. Understanding and selecting the right approach is critical before starting. To find the best cyber security approach, you can consult with CyberUnlocked so that the right scan is conducted to best suit your business needs.
How often should you run a cyber security scan?
Cyber security scanning is an ongoing process. Though scans can be a one-time assessment, it’s best to have cyber security auditors like CyberUnlocked perform a continual evaluation of your business. This allows for continuous protection of your company’s infrastructure and helps deal with any changes to your systems (such as the introduction of new applications or devices) or new security vulnerabilities found by criminals that may pose a cyber security threat to your business.
If continuous scanning is not possible, the frequency of scans can vary from weekly or monthly to annually. So, what’s the minimum amount of time between scans? The answer is it depends on many risk and business factors, consideration of your industry, your risk appetite, your compliance needs and your customer’s expectation.
Where to start?
Contact CyberUnlocked to tailor a cyber security audit that best fits your business. What’s more, we can conduct the audit and manage your security vulnerabilities. We investigate your systems to determine the areas where they are most vulnerable to external threats and provide solutions to safeguard your business infrastructure.
More CyberUnlocked Blogs